
UserAssist Forensic Artifacts: What they are and how to use them
What is the UserAssist artifact?
UserAssist is a feature in Windows that tracks the usage of executable files and applications launched by the user. This data is stored in the Windows Registry and can be critical for forensic analysts seeking to reconstruct a timeline of user activity.
You’ll find a particularly powerful example at the end of this blog, which details a recent child sexual exploitation case where a minor detail from the child’s forensic interview became the turning point in securing a conviction.
Where to find UserAssist
Specifically, UserAssist resides within the NTUSER.DAT hive under:
Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssistEach entry in UserAssist is ROT13-encoded, and Magnet Axiom automatically decodes this information for easy review. The decoded data includes:
- Application path or identifier
- Run count
- Last execution timestamp (in FILETIME format)
- Focus time (how long the app remained active/in focus)
- Focus count (how often the window was brought to the foreground)
Depending on the version of Windows, Microsoft has expanded the detail and granularity of the data captured:
- Windows XP/2000: Captured basic details like application path, run count, and last execution time
- Windows Vista/7: Introduced Focus Time, allowing insight into how long an application was actively used
- Windows 8: Increased the precision of focus time logging
- Windows 10/11: Added detailed tracking of Universal Windows Platform (UWP) applications (e.g., apps from the Microsoft Store). Now analysts can identify not just app launches, but specific user activities within a UWP app
This artifact offers valuable insight into GUI-based interactions on a Windows system. It reveals not just what applications were opened, but also how often they were used and for how long.
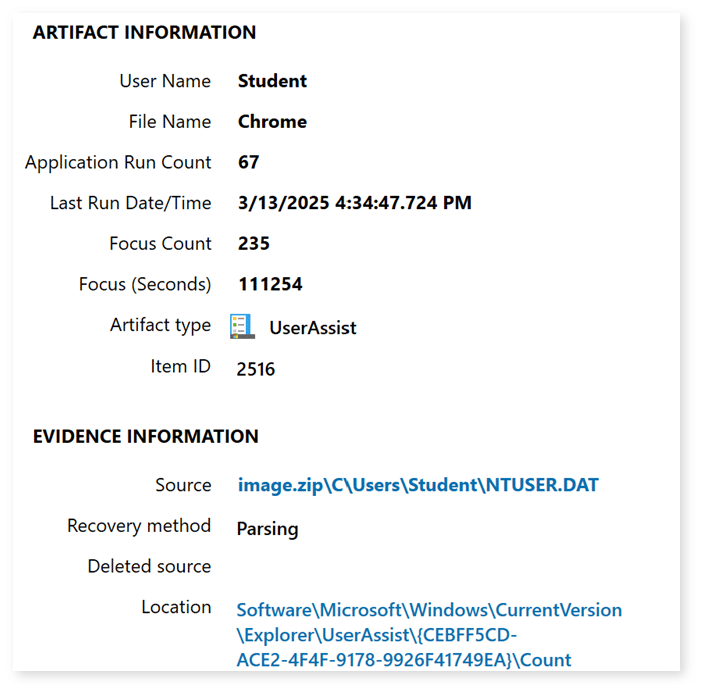
If we examine the UserAssist data location above, we see the expected path of Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\
Next in the path, we see a Globally Unique Identifier, or GUID. This GUID correlates to the type of tracked user activity:
Windows 7 and above:
{CEBFF5CD‑ACE2‑4F4F‑9178‑9926F41749EA}
Identifies application or executable launches, programs run directly via .exe files
{F4E57C4B‑2036‑45F0‑A9AB‑443BCFE33D9F}
Corresponds to launches initiated via shortcuts, which includes clicks on .lnk files
Windows XP:
{0D6D4F41-2994-4BA0-8FEF-620E43CD2812}: A key specific to IE7
{5E6AB780-7743-11CF-A12B-00AA004AE837}: IE Favorites and other IE toolbar objects
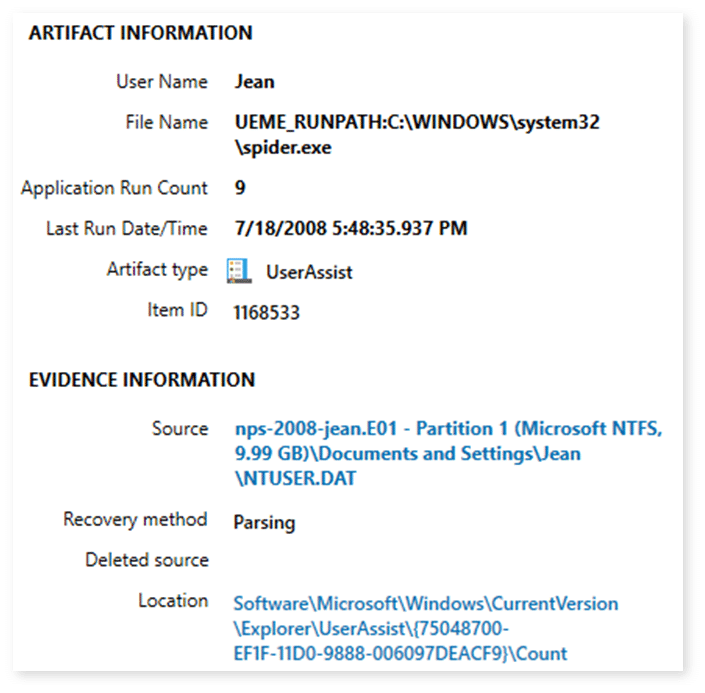
{75048700-EF1F-11D0-9888-006097DEACF9}: Applications, files, links, and other objects that have been accessed.
Finally, the UserAssist data is located in \Count.
**Caution**
Shortcut (.lnk) interactions can register without actual execution, emphasizing the importance of verifying genuine app usage via Focus Time.
What is Focus Time and why it matters
Focus Time in the UserAssist artifact represents the cumulative amount of time in milliseconds that a given application window was active in the foreground. This means it had user focus on the desktop.
Focus Time is a registry-tracked measure of how long a specific application remained the active window on the user’s desktop. It is recorded as an integer in milliseconds and reflects foreground window status, not actual user interaction.
Why Focus Time Matters in forensics:
- Entries with positive Focus Time are a strong indicator that the application was actually run and remained open, helping validate genuine user activity.
- Entries with zero Focus Time may result from shortcut interactions where a user clicks a Start Menu or desktop icon but the application never fully launches or loads in the foreground.
Important caveats:
- AFK time is still counted. If a user opens an application and walks away, the timer continues as long as that window remains in focus.
- Clicking on a shortcut can register an entry even if the executable fails to launch or is immediately closed.
- Automated processes, such as shell preloading or Windows refreshing shortcuts, may generate UserAssist entries without conscious user action.
How Focus Time Is calculated:
- Windows increments Focus Time each time the app gains focus and remains in the foreground.
- The value is cumulative and not broken down into session-level detail.
- The calculation methodology is not publicly documented by Microsoft, resulting in variations in interpretation.
- Some debate exists about how precisely and consistently Windows tracks this time, especially across different builds or during fast application switches.
Forensic interpretation guidance:
- Treat non-zero Focus Time as supporting evidence of real execution, especially when aligned with AmCache, Prefetch, and SRUM data.
- Treat zero Focus Time and non-zero Run Count as potentially ambiguous. This suggests a click or launch attempt that may not have resulted in an actual run.
From a Windows XP UserAssist artifact (Pre-inclusion of Focus Count/Focus Time):
Limitations and investigative considerations
- Logs GUI-driven interactions; lacks command-line or background process visibility.
- User settings can disable or clear history, affecting completeness.
- Always validate with complementary artifacts (Prefetch, Jump Lists, SRUM, AmCache).
Using Magnet Axiom for UserAssist analysis
Magnet Axiom efficiently parses UserAssist artifacts by decoding ROT13 entries, extracting relevant timestamps, run counts, and focus metrics. Its powerful visualization tools aid analysts in rapidly establishing user activity timelines.
UserAssist examples in solving a real-world case
In a recent child sexual exploitation case, a minor detail from the child’s forensic interview became the turning point in securing a conviction. The child recalled being shown “videos of naked people” on a computer and said the suspect would use a “traffic cone” to play the videos.
That description was immediately apparent to be VLC Media Player, a popular open-source video player known for its orange cone icon and its ability to chew through most types of videos, even if damaged, making it a popular video player in the child exploitation realm.
This detail was brought up in a suspect interview, where he confidently denied ever using VLC Media Player. Initially, the forensic examination of the computer appeared to support his claim as the application wasn’t installed on the system at the time of seizure, and there were no obvious traces in standard forensic artifact locations.
However, a deeper dive into the Windows registry, specifically the UserAssist key, told a different story.
The UserAssist key, located in the Windows Registry, tracks user interaction with executables and shortcuts, essentially logging application usage even after a program has been uninstalled. Examination of this key revealed that VLC had been executed at least 17 times on the suspect’s profile.
This evidence directly contradicted the suspect’s statement and corroborated the child’s account. While VLC itself was no longer present, the remnants in the registry were significant, helping build a timeline of usage and strengthening the overall case. This is a powerful reminder that in digital forensics, even when visible traces are gone, the system often still holds the truth. The UserAssist key proved an essential piece of evidence in exposing a critical lie and ensuring justice was served.
Learn more about Magnet Forensics products like Magnet Axiom and Magnet One to help accelerate your investigations to close more cases, faster.