
Blueprint of an eDiscovery Investigation: Digital forensics and eDiscovery
Introduction
As the volume and variety of electronically stored information continues to grow, legal and investigative teams encounter increasing complexity in their search for evidence. Successfully managing a modern investigation requires a coordinated approach that integrates legal expertise, advanced digital forensics, and efficient eDiscovery workflows.
This blog or “blueprint” will examine the intersection of digital forensics and eDiscovery, providing strategies, tools, and best practices that ensure electronic evidence is identified, preserved, and presented in a reliable, defensible, and comprehensive manner.
What is eDiscovery?
Electronic discovery, or eDiscovery, is the process of collecting, reviewing, and exchanging electronically stored information (ESI) for use as evidence in legal cases. eDiscovery is specific to digital evidence including data from various electronic sources such as email accounts, social media, databases, websites, and more. ESI must be preserved in a specific way to ensure its legal use.
As electronic data becomes increasingly fragmented and dispersed across endpoints, cloud platforms, and mobile devices, organizations face unprecedented challenges in identifying, collecting, reviewing, and scoping potentially relevant information.
Magnet Forensics addresses these challenges head-on with innovative solutions like Magnet Axiom Cyber, Magnet Verakey, and Magnet Nexus. These solutions empower legal and investigative teams to efficiently collect, process, and analyze data from even the most complex environments, ensuring collections are forensically sound, comprehensive, and defensible.
By seamlessly bridging the gap between traditional eDiscovery and advanced digital forensics, we help organizations streamline workflows, reduce risk, and gain deeper insights from electronic evidence, no matter where it resides.
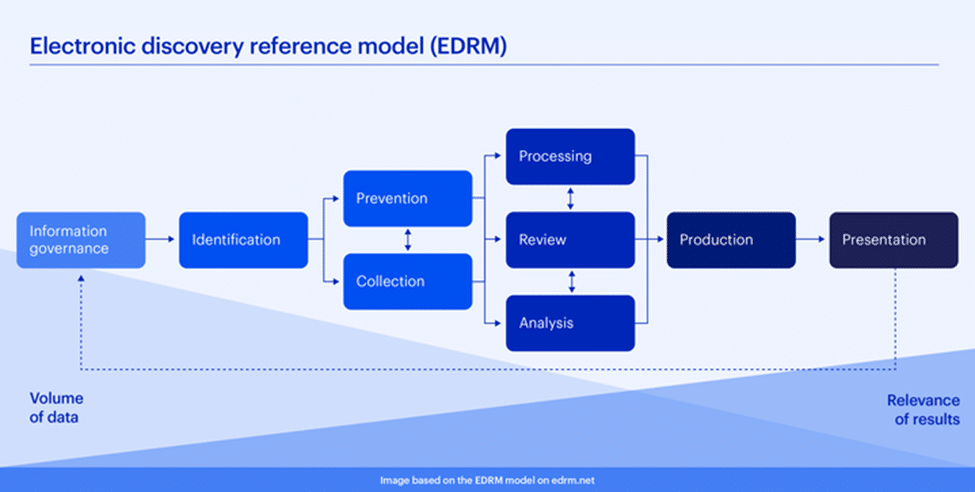
Understanding the EDRM framework
Source: https://edrm.net/edrm-model/current/
The EDRM provides a structured framework for managing electronic evidence throughout litigation or regulatory investigations.
It guides legal professionals through organized, repeatable, and defensible steps, from initial information governance and identification through production and presentation, ensuring that electronic evidence is handled efficiently, securely, and in compliance with legal requirements.
Here’s a brief overview of each EDRM phase:
- Information governance: Establish policies to manage electronic information responsibly, ensuring compliance, and reducing eDiscovery risks and costs.
- Identification: Locate potential sources of electronically stored information (ESI) relevant to a legal case or investigation.
- Preservation: Protect identified ESI from alteration or destruction through legal holds and secure storage.
- Collection: Gather ESI from its original sources in a forensically sound manner, ensuring integrity and admissibility.
- Processing: Reduce data volumes and convert ESI into reviewable formats, typically through filtering, deduplication, indexing, and metadata extraction.
- Review: Examine collected data to determine relevance, responsiveness, privilege status, and confidentiality.
- Analysis: Evaluate ESI for patterns, context, and relationships to develop insights relevant to the case strategy.
- Production: Deliver ESI to opposing parties or regulatory authorities in agreed-upon formats, maintaining defensibility and authenticity.
- Presentation: Display ESI clearly and persuasively during legal proceedings, including trials, depositions, or regulatory hearings.
The eDiscovery process typically involves collaboration among multiple professionals across legal, technical, and compliance fields. Participants include:
- Attorneys (both in-house counsel and external law firms) who provide legal oversight
- eDiscovery specialists and paralegals who manage the operational aspects
- IT and DFIR personnel who handle data identification and collection
- Digital forensic analysts who ensure data integrity and defensibility
- Compliance officers who assist with information governance.
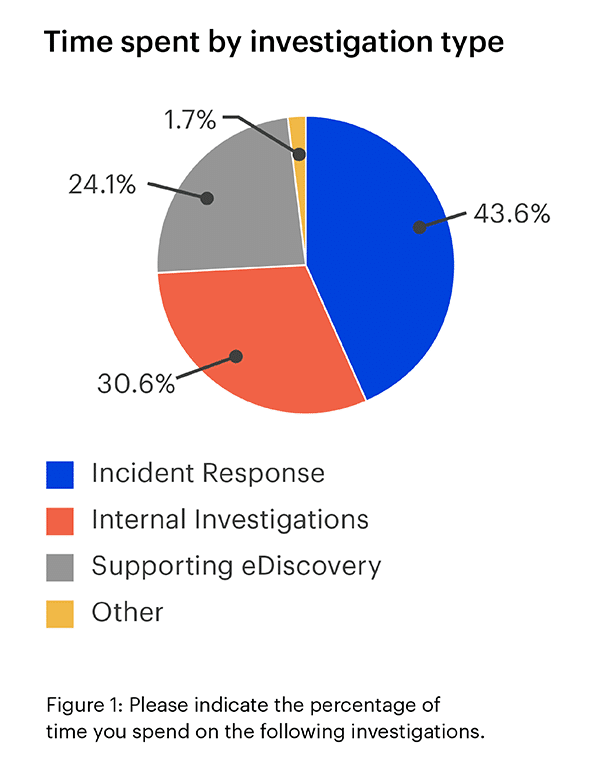
According to the 2025 State of Enterprise DFIR Report, DFIR professionals spent 24.1% of their time supporting eDiscovery-related investigations. While eDiscovery is often associated with civil litigation cases, it is also used for internal investigations, mergers and acquisitions, and regulatory investigations.
What is digital forensics and what role does it play in the EDRM cycle?
Digital forensics and eDiscovery, while both integral to managing electronic evidence, serve distinct roles within legal and investigative contexts. Digital forensics is a specialized field focused on identifying, preserving, and analyzing digital evidence, often in scenarios where data is not readily accessible to the general user. It requires specialized software and deep technical knowledge of various computer operating systems, networking, scripting, memory analysis, in addition to legal knowledge and an investigative mindset.
Forensic experts employ specialized tools and methodologies to recover such data, ensuring its integrity for use in legal proceedings. This process is meticulous, aiming to maintain a clean chain of custody and adhere to legal requirements for evidence admissibility. Digital forensics is crucial in situations involving cyber incidents, internal investigations, or any case where the authenticity and origin of digital data are in question.
How are digital forensics and eDiscovery different?
Digital forensics and eDiscovery, while both focused on managing electronic evidence, serve distinct roles within investigations and legal proceedings. Digital forensics is a specialized discipline dedicated to the identification, preservation, and in-depth analysis of data, often in situations where information has been deleted, hidden, or is otherwise not easily accessible. It requires software that can deeply dive into operating systems and devices to uncover and reconstruct digital events, maintain a strict chain of custody, and ensure the integrity and admissibility of evidence.
On the other hand, eDiscovery operates within a legal framework and concentrates on the efficient identification, collection, review, and production of electronically stored information (ESI) that is readily accessible. While eDiscovery is designed to organize and streamline large volumes of data for legal review, it typically does not recover deleted or hidden artifacts the way digital forensics solutions and methodologies can. In many complex cases, digital forensics is relied upon first to uncover and secure all relevant data, including material invisible to standard eDiscovery tools, before the information enters the broader eDiscovery review and production process.
Complex data challenges in eDiscovery
As data becomes more abundant, diverse, and spread across various endpoints, legal and investigative teams face growing challenges in managing electronically stored information. These difficulties can slow down eDiscovery processes and make it harder to ensure they are defensible, especially in complex or high-stakes cases. Common obstacles include:
A workforce that is geographically dispersed
- Investigations often involve employees across multiple time zones or jurisdictions, making coordinated, remote data collection difficult
Fragmented data across numerous platforms
- Data lives in many places: email servers, cloud storage, and collaboration tools, making it hard to identify and collect everything comprehensively
Data volume and variety
- The sheer amount and diversity of data types increases review time and raises costs
Timeliness of collections/review
- Delays in collecting and reviewing data can impact legal deadlines and jeopardize case outcomes
Ensuring the most complete data collection, so no data is missed
- Missing even a single relevant file can create risk, especially if opposing counsel later uncovers it
Chain of custody
- Maintaining clear documentation of who handled data and when is essential to preserving its admissibility in court
Reducing overcollection
- Gathering excessive irrelevant data increases storage costs and clutters the legal review process
Adherence to data privacy regulations
- Investigations must comply with privacy laws, especially when handling sensitive personal or international data
Adherence to the scope of the investigation
- Straying beyond the defined legal scope can result in unnecessary exposure, wasted resources, or legal sanctions
Benefits of digital forensics in eDiscovery
Digital forensics brings significant value to the eDiscovery process by enhancing the thoroughness, defensibility, and reliability of electronic evidence handling.
Where the two disciplines intersect, digital forensics ensures data is identified, collected, and preserved with integrity and provenance intact—all key requirements for admissibility in court. Forensic tools can recover deleted, hidden, or encrypted files that might otherwise be missed by traditional eDiscovery methods, providing a more complete picture of the evidence.
This capability is especially valuable in complex cases involving allegations of data manipulation, insider threats, or cyber incidents, where establishing a clear chain of custody and documenting each step of evidence handling is crucial. By leveraging digital forensics in eDiscovery, organizations gain confidence that all potentially relevant data is accounted for, and the evidence will withstand legal scrutiny, ultimately reducing risks of spoliation, sanctions, or overlooked facts during legal review.
What are the risks of confusing Digital Forensics and eDiscovery?
Confusing digital forensics with traditional eDiscovery can pose serious risks, especially when a complete and defensible evidence trail is needed. Traditional eDiscovery tools typically collect only user-accessible data, often missing key evidence like deleted files, hidden artifacts, metadata, or system logs that require forensic expertise. This can lead to under-collection, where important data is overlooked, or over-collection, where excessive, unfocused data complicates review time and increases costs.
Skipping forensic best practices during data collection and preservation can lead to data spoliation, compromising the integrity and chain of custody, and potentially making evidence inadmissible in court. When organizations fail to use digital forensics where it’s needed, they risk missing critical evidence, facing legal sanctions, or falling short of discovery obligations, all of which can jeopardize the outcome of their legal or investigative efforts.
What are the best practices for digital forensics and eDiscovery working together?
Best practices for integrating digital forensics and eDiscovery begin with clearly defining the roles and responsibilities of each team. Establishing well-documented protocols for evidence handling, chain of custody, and secure storage is essential to maintain compliance and protect against data spoliation. Collaborative planning then becomes an integral part of the workflows. Finally, using the right mix of forensic and eDiscovery tools, such as Axiom Cyber, for deep data recovery and defensible collection, ensures that all relevant data is both discoverable and admissible, maximizing efficiency and minimizing legal risk. We’ve outlined the steps below:
1. Define roles and responsibilities
- Clearly establish the roles of digital forensic and eDiscovery teams
- Digital forensic experts should lead the identification, preservation, and forensic acquisition of data, ensuring its integrity and defensibility
- Engage legal and eDiscovery professionals early to clarify:
- The scope of collection
- Key custodians
- Types of data required for review and production
2. Establish well-documented evidence protocols for:
- Evidence handling
- Chain of custody
- Secure storage
- Maintain compliance and protect against data spoliation
3. Collaborative planning
- Hold joint planning sessions at the beginning of each case
- Align priorities and timelines between disciplines
- Anticipate potential challenges and streamline workflows
4. Leverage appropriate tools
- Use a combination of forensic and eDiscovery tools (e.g., Axiom Cyber) for deep data recovery and defensible collection.
- Employ review platforms optimized for legal workflows.
- Ensure all relevant data is discoverable, admissible, and handled efficiently to minimize legal risk
Why end-to-end solutions help your eDiscovery cases
As data volumes grow and become more dispersed across devices and platforms, legal and investigative teams require more than what traditional eDiscovery platforms can offer. These tools are often limited to logical collections, capturing only user-accessible files, and lack the forensic depth needed to uncover deleted, encrypted, or hidden data.
A modern, full-spectrum solution bridges this gap by integrating digital forensics capabilities into eDiscovery workflows. With access to the full file system, investigators can recover critical evidence that may otherwise be missed, ensuring a more complete and defensible case.
This approach supports:
- Comprehensive data collection: Acquire evidence from a wide range of sources including computers, mobile devices, remote custodians, and cloud services to ensure no relevant data is left behind.
- Targeted collection for cost control and compliance: Minimize data volume and reduce legal review costs by collecting only what is necessary. Targeted filtering helps maintain focus and meet compliance requirements.
- Seamless collaboration: Share evidence efficiently and securely. Export in Relativity Short Message Format (RSMF) or use tools like Magnet Review to collaborate with legal teams and external partners—without compromising the integrity of the data.
By uniting forensic depth with eDiscovery efficiency, organizations can gain a clearer understanding of the facts, reduce risk, and better support the success of legal and investigative outcomes.
How can Magnet Forensics help your eDiscovery cases?
Magnet Forensics strengthens your eDiscovery process by combining digital forensics with targeted data collection. Recover deleted, encrypted, or hidden evidence across devices, streamline collaboration, and ensure a complete, defensible case—, while reducing review costs, and meeting compliance requirements. Here are more details about how our solutions help your workflows:
Cloud-based forensic data collection
Ideal for conducting collections across geographically dispersed networks of endpoints, including laptops, desktops, and external drives.
- Facilitated by Magnet Nexus, enabling efficient and secure collections without physical access
- Nexus collections are defensible, forensically sound, and minimally disruptive to end-users
- Particularly beneficial in environments with hybrid or fully remote workforces, simplifying data collection regardless of the physical location of devices
Endpoint-based collection
- Can target full disk images or selected paths, files, and artifacts (e.g., user documents, browser history, registry keys)
- Tools like Magnet Axiom Cyber can be used for defensible, remote collections
- Supports agent-based remote access, crucial in modern hybrid/remote work environments
Mobile device collection
- Increasingly important due to the prevalence of business communications via mobile apps like WhatsApp, Signal, SMS, iMessage, and Teams
- Collections are performed from Android and iOS devices using forensic tools like Magnet Verakey
- Depending on device access, collection may be:
- Logical (files, databases, app data, contacts, call logs, etc.)
- Full File system (includes hidden/system files)
- Mobile collections often require legal authorization and device access and may involve coordination with employees, legal, and IT
Complete case analysis
In Axiom Cyber, you get a more complete parsing and presentation of the digital forensic artifacts than your eDiscovery software suites. The ability to load all of the possible data sources into one Axiom Cyber case provides some powerful options when it comes to culling the data before loading it into the eDiscovery platform of your choice. Here are some of the sources that you can load and search across in Axiom Cyber:
- Workstation and laptop endpoints
- Mobile devices
- Cloud storage and collaboration platforms
- Microsoft 365 (Exchange Online email, OneDrive, SharePoint, Teams chats and files)
- Google Workspace (Gmail, Google Drive, Google Chat, Calendar)
- Dropbox, Box, and other file-sharing services
- Slack, Zoom, and other collaboration tools
- Virtual machine disk images (VMware, Hyper-V, VirtualBox)
- Removable media
The ability to search and cull data across a more complete set of collected and processed data by Magnet Forensics software and hardware ensures you look at a more complete picture. Some of this data could be responsive to the eDiscovery request. There is a significant risk in not providing the complete data by not utilizing these tools in your eDiscovery request.
Digital artifacts unique to digital forensic software and their value
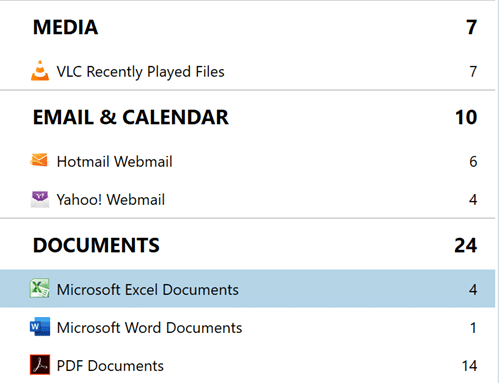
1. Deleted files and folders
- Magnet’s solutions surface deleted files and folders from data recovered from unallocated space or after deletion (not visible to users or standard eDiscovery tools).
- Why it matters to eDiscovery: These files are often missed by standard eDiscovery tools but may contain highly relevant information, especially in cases of intentional deletion or spoliation. Their recovery can be critical in proving intent or uncovering hidden evidence.
- This was data recovered from fully deleted files on a Windows endpoint:
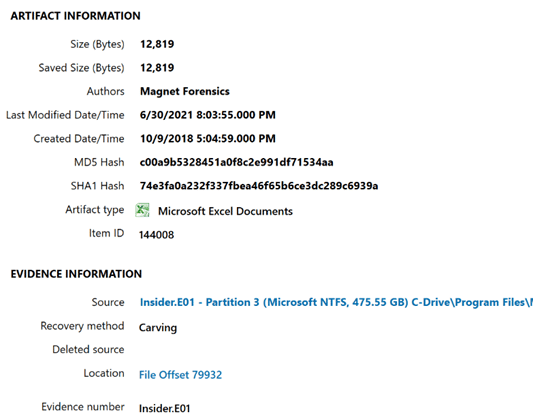
- Looking at one of those Excel artifacts, we can see the file was fully recovered by Axiom Cyber:
- Looking at one of those Excel artifacts, we can see the file was fully recovered by Axiom Cyber:
2. File system metadata
- Timestamps (creation, modification, access, deletion)
- File system journal records (e.g., $LogFile, $MFT in NTFS)
- Alternate data streams (ADS) in NTFS
- Why it matters to eDiscovery: Metadata like timestamps and journal records can establish when documents were created, accessed, modified, or deleted—crucial for timelines, authenticity, and validating user actions. In addition, these artifacts can be critical in setting a timeline for events around an incident/collection.
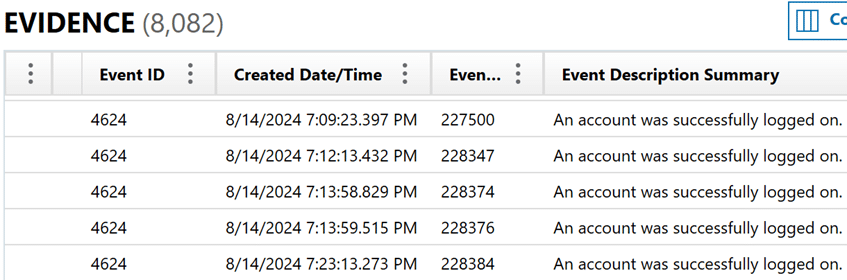
3. System and application logs
- Windows event logs (e.g., Security, application, system logs)
- Application-specific log files (including those not stored in user folders)
- Why it matters to eDiscovery: Logs provide detailed, time-stamped records of system activity, including user logins, program execution, and error events. They can support or contradict testimony and help reconstruct the context around key actions.
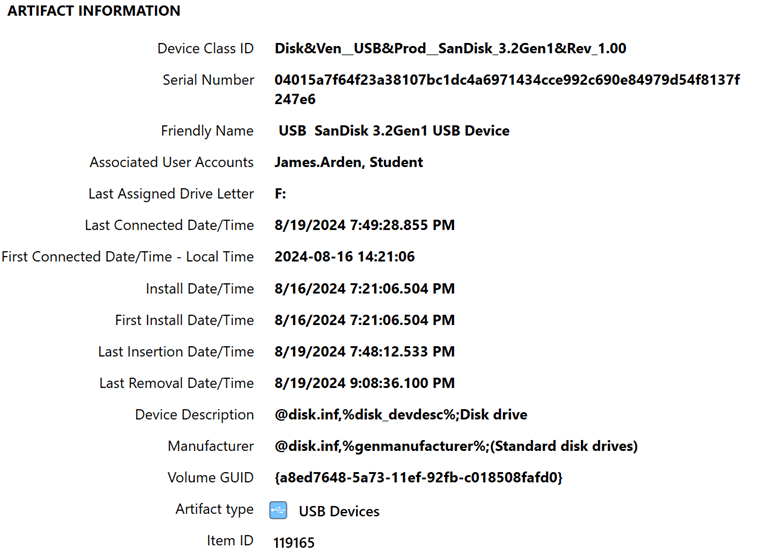
4. Registry artifacts (Windows)
- User activity traces (e.g., MRU lists, USB device history)
- Installed software, user accounts, and network settings
- Why it matters to eDiscovery: Registry entries offer insights into user behavior, software usage, device connections, and configuration changes. They help identify custodians, usage patterns, or unauthorized activity.
5. Shadow copies and volume snapshots
- Previous versions of files and system states
- Why it matters to eDiscovery: These artifacts allow recovery of prior file versions or system states, which may contain earlier drafts, deleted content, or configurations that are no longer visible.
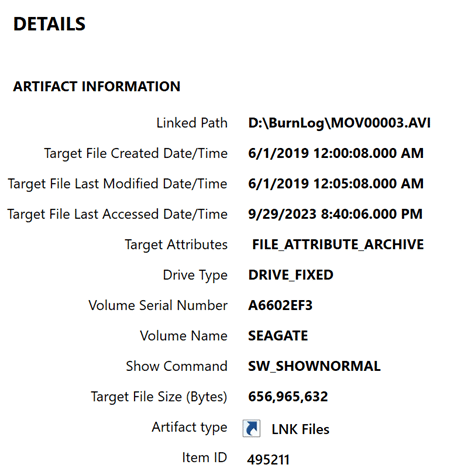
6. Prefetch, jump lists, and LNK (Shortcut) files
- Evidence of program execution and recent file access
- Why it matters to eDiscovery: These reveal which applications were run and which files were accessed recently. They offer supporting evidence of user intent or relevance that may not appear in email or document review.
7. Memory (RAM) captures
- Live memory artifacts (running processes, decrypted passwords, chat fragments, volatile data)
- Why it matters to eDiscovery: Memory captures can reveal transient data like passwords, chat messages, or encryption keys—critical in cyber-related cases or where data access needs to be proven.
8. Network artifacts
- Connection history, Wi-Fi profiles, ARP cache
- Firewall and proxy logs
- Why it matters to eDiscovery: Connection logs and network configurations can help attribute activity to specific users or devices, show data movement, and identify possible exfiltration routes or remote access.
9. Artifacts of anti-forensic activity
- Evidence of data wiping, file shredding, encryption, or obfuscation attempts
- Why it matters to eDiscovery: Evidence of file wiping or encryption can support claims of data destruction or obstruction of justice, which may carry legal consequences or influence sanctions.
10. Mobile device artifacts only located on a full file system
- Traditional eDiscovery tools typically extract only user-accessible data like visible documents, photos, texts, and emails from mobile devices. Magnet Verakey goes further with full file system extractions, uncovering deleted data, app content, system logs, metadata, and hidden artifacts. This deeper access is critical for recovering communications, verifying data integrity, reconstructing timelines, and identifying concealed evidence, ultimately strengthening the reliability and defensibility of the eDiscovery process.
Here are extractions from the same cell phone, one using a logical extraction, the other using an advanced Verakey full file system extraction:
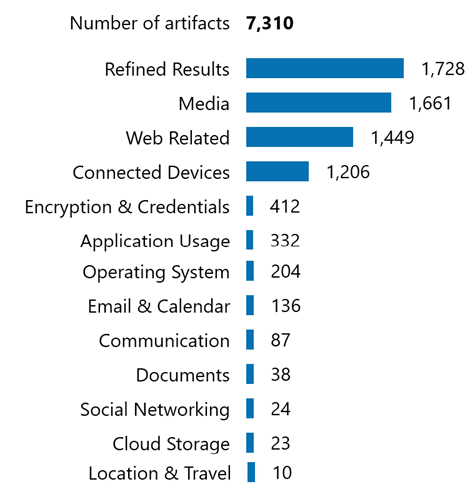
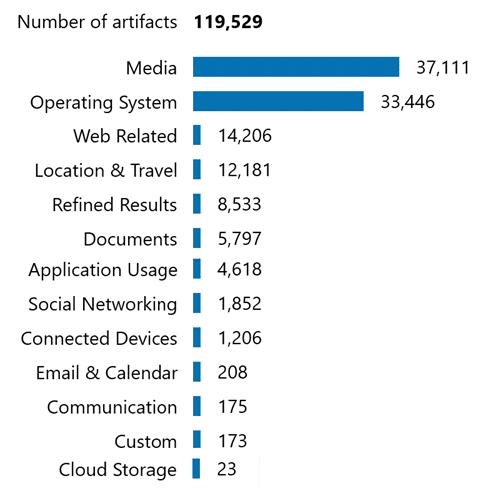
In the example above, two extractions from the same device, one logical and one full file system via Verakey, illustrate the difference. The full extraction revealed emails, location data, communications, web activity, and system information that could prove critical to the investigation or legal request.
Conclusion
Integrating digital forensics into eDiscovery workflows is essential for managing complex electronic evidence in today’s data-rich environment. Clearly defined roles, rigorous evidence-handling protocols, proactive collaboration, and the strategic use of specialized tools such as Magnet Axiom Cyber and Verakey enable organizations to confidently identify, preserve, and present defensible evidence. By adopting these best practices, legal and investigative teams can minimize risks, enhance efficiency, and ensure the integrity and admissibility of electronic evidence throughout the eDiscovery lifecycle.