
How to execute defensible, comprehensive legal holds with digital forensics
When business data is distributed across cloud platforms, remote endpoints, mobile devices, and virtual systems, organizations face complex challenges responding to litigation or regulatory events, such as legal holds for eDiscovery investigations. Legal teams must not only identify and preserve electronically stored information (ESI) but also ensure the authenticity, integrity, and defensibility of the evidence collected.
The importance of digital forensics in legal holds and eDiscovery
Digital forensics is the science and methodology of identifying, preserving, and analyzing digital evidence, often when it’s hidden, deleted, or otherwise inaccessible to standard eDiscovery tools. By integrating digital forensics capabilities into the legal hold process, organizations can:
- Recover deleted or hidden files critical to the matter
- Analyze metadata and system logs for context and timelines
- Preserve the integrity of data and maintain a verifiable chain of custody
- Ensure evidence stands up to legal scrutiny and meets court standards for admissibility
- Minimize risk of spoliation and avoid sanctions by maintaining evidence defensibility
This approach bridges the gap between basic legal hold management and the investigative rigor required in today’s legal and regulatory environment.
What digital forensics is not
It’s important to recognize that digital forensics solutions are not designed to manage or execute legal holds themselves. They do not replace legal hold management systems or processes for issuing, tracking, or releasing holds. Instead, their role is to assist legal and compliance teams by ensuring collections are thorough and forensically sound. While digital forensics cannot monitor compliance or provide automated hold notifications, it plays a critical supporting role by uncovering hidden or deleted data sources that traditional eDiscovery tools may miss. Relying solely on standard collection methods can raise the risk of incomplete preservation and missed evidence, underscoring the value of digital forensics as a complement to established legal hold workflows.
What are legal holds?
A legal hold, also known as a litigation hold, is a process organizations implement to preserve all relevant information when litigation is reasonably anticipated or underway. It ensures ESI and physical documents are not modified, deleted, or otherwise destroyed.
Key components of a legal hold process
- Triggering event: Initiated when a lawsuit is filed, a regulatory investigation begins, or litigation is reasonably anticipated
- Custodian identification: Identify individuals likely to possess relevant data based on their roles, actions, or communications
- Preservation instructions: Communicate to custodians which data (emails, files, device content) must be preserved
- Scope definition: Determine the time range, data types, devices, and locations subject to the hold
- Monitoring and compliance: Track compliance through acknowledgments, automated systems, or periodic updates
- Release: When the legal obligation ends, custodians are notified they may resume standard data management
Implementing a robust legal hold process is essential to compliance, minimizing the risk of spoliation, and demonstrating defensible practices in court. However, traditional approaches alone may miss crucial evidence, especially as data becomes more fragmented across systems.
How digital forensics solutions enhance legal holds
Digital forensics solutions, such as Magnet Nexus, Magnet Axiom Cyber, and Magnet Verakey, play a crucial, complementary role in the legal hold process:
Expanded evidence discovery and preservation
- Goes beyond the user-visible layer: Forensic tools can recover deleted data, extract hidden artifacts, analyze metadata, and reconstruct timelines, surfacing evidence traditional eDiscovery solutions may miss.
- Full file system access: Forensic collections can access system and application logs, shadow copies, memory dumps, network activity, and anti-forensic indicators (such as evidence wiping or encryption), ensuring a truly comprehensive hold.
- Mobile device artifacts: Full file system extractions from mobile devices can recover app data, deleted messages, and logs often overlooked by standard collections.
Chain of custody and integrity
- Provenance and documentation: Digital forensic solutions meticulously record acquisition details, generate hashes, and provide logs, supporting defensible chain of custody.
- Preservation of volatile data: Forensics can capture RAM, active sessions, or temporary files that could be lost if not collected promptly.
Efficiency, focus, and risk reduction
- Targeted collections: Collect only relevant custodial data, reducing unnecessary review and limiting exposure of privileged or sensitive information.
- Rapid, scalable, and remote: Tools like Magnet Nexus enable silent, remote collection at scale, ideal for dispersed workforces or sensitive investigations.
- Cost and time savings: Targeted forensic collections minimize data storage and review costs compared to indiscriminate full disk imaging.
Legal defensibility
- Enhanced defensibility: Forensically sound collections are easier to document, defend, and justify under proportionality and privacy requirements. Forensic analysis helps build timelines, validate evidence, and avoid adverse inferences.
Use cases
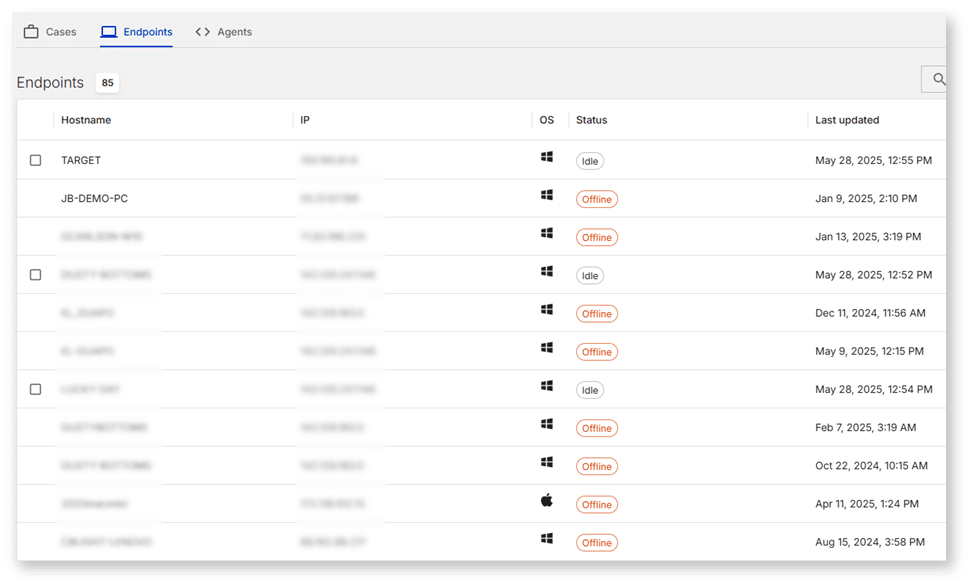
SaaS-based legal hold and collection with Magnet Nexus
Scenario: An internal compliance team receives an anonymous report of financial misconduct. Legal anticipates litigation and issues a legal hold.
- Digital forensics in action: Nexus supports global, remote, and covert data collection by acquiring not only user files but also system logs and application artifacts. All activity is logged for defensibility.
- Benefits: Rapid, scalable holds and collections across endpoints, maintaining data integrity and chain of custody, while minimizing disruption. Rapid preservation through timely collection reduces the chances for data spoilage.
Targeted artifact collection with Magnet Axiom Cyber
Scenario: An employee is investigated for suspected IP theft; a legal hold is issued, and targeted forensic data is needed.
- Digital forensics in action: Axiom Cyber collects file access logs, deleted files, USB histories, cloud storage interactions, and other hidden artifacts, going far beyond a standard document collection. Volatile data (like browser sessions and RAM) can be preserved as well.
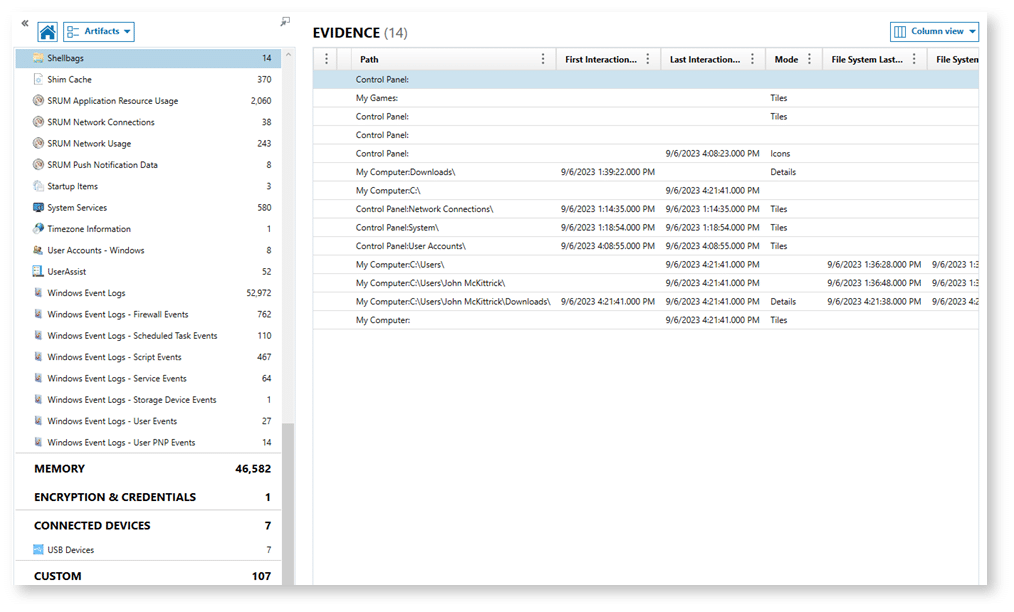
- Benefits: Collection is focused and fast, reducing unnecessary review, limiting privacy exposure, and strengthening the defensibility of the process. Findings are exported in review-ready formats for legal analysis. These export options include RSMF exports and a load file ready for importation into the eDiscovery platform of your choice. A full disk collection can be implemented if required by the collection parameters.
- Targeted scope: The examiner collects only relevant paths and artifacts rather than imaging the full disk, reducing review time. These targeted collections have numerous advantages over a full disk image:
- Scope control:
- Targeted collections: Collect only relevant custodial data (e.g., docs, email, chats)
- Full disk imaging: Collects OS, apps, system, and user data indiscriminately
- Efficiency:
- Targeted collections: Fast, remote, non-disruptive
- Full disk imaging: Time-intensive and disruptive
- Cost savings:
- Targeted collections: Minimizes review and hosting costs
- Full disk imaging: Drives up total cost of eDiscovery
- Risk reduction:
- Targeted collections: Limits exposure of sensitive or privileged data
- Full disk imaging: Captures potentially unnecessary data
- Defensibility:
- Targeted collections: Easier to document and justify scope
- Full disk imaging: Harder to defend under proportionality principles
- Scope control:
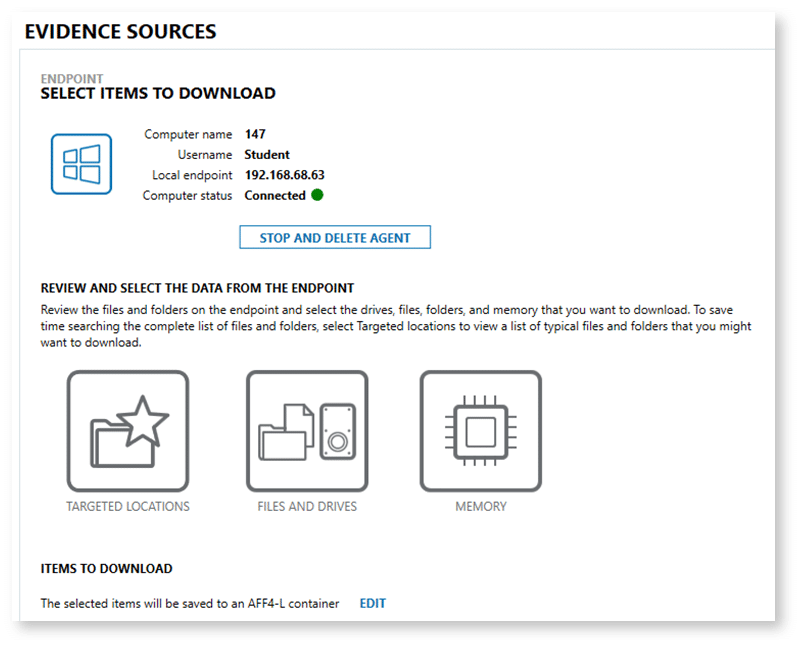
Targeted mobile communication collection with Magnet Verakey
Scenario: During an internal investigation into potential regulatory violations, a legal hold is issued for all relevant communications involving the CEO. Many of the suspected communications occurred through a third-party messaging application installed on the CEO’s mobile device. This app’s data is stored in a location only accessible through a full file system extraction, meaning a logical acquisition would miss critical messages entirely.
How Magnet Verakey supports this workflow:
- Full file system access: Verakey can perform a full file system extraction to capture the application’s hidden and system-level data, including chat histories, attachments, and metadata.
- Category-based targeting: Instead of collecting the device’s entire contents, which could introduce privacy risks and create unnecessary review burden, Verakey allows the examiner to target the specific “communications” category for extraction. This category-based extraction takes place at the full file system level, ensuring no data is missed.
- Reduced risk of over-collection: This targeted approach ensures that only relevant communications are preserved, minimizing exposure to unrelated information.
- Defensibility and integrity: Verakey’s forensic process maintains the authenticity of the recovered messages, with hashes and logs for chain-of-custody documentation.
- Benefits: By combining the depth of a full file system extraction with the precision of category-based targeting, Verakey enables legal teams to collect exactly what’s needed for the legal hold, ensuring no critical evidence is missed while avoiding unnecessary over-collection.
Best practices for integrating legal hold and digital forensics
- Engage forensic experts early in the legal hold process to ensure scope, protocols, and tools are defined.
- Use forensically sound methods and maintain comprehensive documentation.
- Prioritize targeted, artifact-level collections over indiscriminate full-disk imaging to optimize efficiency and reduce risk.
- Leverage the strengths of both legal and forensic teams for a holistic, defensible response.
Discover an easier, more defensible way
Legal holds are a foundational part of defensible eDiscovery. Tools like Magnet Nexus and Magnet Axiom Cyber extend the reach and reliability of legal hold execution by enabling scalable, targeted, and remote collections. Nexus excels in enterprise-wide, quiet collections across endpoints, while Axiom Cyber allows deep forensic dives into specific custodians or endpoints. Contact Magnet Forensics and learn more about taking a modern, comprehensive approach to legal hold compliance.of legal hold execution by enabling scalable, targeted, and remote collections. Nexus excels in enterprise-wide, quiet collections across endpoints, while Axiom Cyber allows deep forensic dives into specific custodians or endpoints. Contact Magnet Forensics and learn more about taking a modern, comprehensive approach to legal hold compliance.
Want to see more eDiscovery content?