
Employee departure: leveraging digital forensics for complete, defensible collections
During an employee departure from an organization, whether through resignation, termination, or other separation, the stakes are high. Without a well-planned approach to data preservation and review, businesses face risks ranging from litigation and regulatory penalties to loss of intellectual property (IP) and exposure of sensitive data.
Traditional eDiscovery processes can collect and preserve accessible data, but they often miss hidden, deleted, or system-level information that could prove critical in employee departure-related matters. This is where digital forensics plays a pivotal supporting role by identifying, recovering, and preserving evidence from across endpoints, cloud accounts, mobile devices, and system artifacts, all while maintaining a defensible chain of custody. Proactively managing data at the time of departure is essential for compliance, protecting valuable assets, and maintaining business integrity. This is particularly crucial if the employee departure involves suspicion of misconduct or the potential theft of proprietary information.
By incorporating digital forensics into the employee departure process, organizations can:
- Recover deleted or hidden files that might indicate attempts to conceal misconduct.
- Analyze metadata and logs to reconstruct timelines of file access, transfers, and communications.
- Preserve volatile or hard-to-reach data such as RAM, application caches, or shadow copies.
- Target collections to avoid over-collection, reducing privacy risks and review costs.
- Prove data integrity with detailed acquisition logs and hash values for court defensibility.
What Digital Forensics Is Not
It’s important to clarify that digital forensic solutions are not designed to manage or issue legal holds or to replace HR/IT offboarding procedures. They do not send hold notices, track acknowledgment, or manage release processes. Instead, their role is to complement these workflows by ensuring the data collections are complete, forensically sound, and include sources that traditional eDiscovery alone might miss. Without this layer, there’s an increased risk of incomplete preservation, under collection, and missed evidence, particularly in complex employee departure cases.
Key components of an employee departure eDiscovery process
- Exit notification: HR or management alerts legal and IT about the employee’s impending or immediate departure.
- Data preservation: Immediately securing digital assets, including emails, files, cloud data, and communications platforms in order to prevent data deletion or exfiltration.
- Access revocation: Promptly disabling account credentials and remote access to reduce security risks.
- Device collection and imaging: Securing endpoint devices (e.g., laptops, mobile devices) for forensic examination, as needed.
- Forensic review: Analyzing preserved data to identify signs of data exfiltration, unauthorized access, or other misconduct.
- Reporting and compliance: Documenting the findings to support potential legal action or regulatory disclosures.
Employee exits can create unexpected legal and security risks, especially when sensitive data or proprietary information is involved. By taking a modern approach to data preservation and review, organizations can simultaneously minimize exposure, ensure compliance, and maintain control over critical information.
How digital forensics enhances employee departure investigations
In the departure context, digital forensics extends the reach and reliability of collections by:
- Identifying and preserving hidden sources: Registry entries, application logs, USB histories, and network connection records can all provide evidence of unauthorized file transfers.
- Recovering deleted evidence: Shadow copies, carved files, and system backups may reveal attempts to wipe devices or destroy incriminating data.
- Capturing mobile device data beyond logical access: Full file system extractions with Verakey can uncover app data, deleted messages, and attachments often missed by standard mobile collections.
- Providing context through timelines: Correlating metadata and system events creates a detailed chronology of actions taken before and after departure.
- Reducing over-collection: Tools like Magnet Verakey can target specific categories (e.g., “communications” or “documents”) from a full extraction, balancing thoroughness with privacy and proportionality.
A structured eDiscovery process at the point of departure isn’t just best practice, it’s a key part of protecting your business. Below we’ll review three common use cases.
Use case 1: Global endpoint data collection with Magnet Nexus for an employee departure
Scenario:
An employee working remotely in a different country resigns suddenly to join a competitor. The company suspects unauthorized data exfiltration.
How Magnet Nexus supports this workflow:
- Immediate remote access: Nexus provides rapid, remote collection from the employee’s endpoint, even internationally, without alerting the employee.
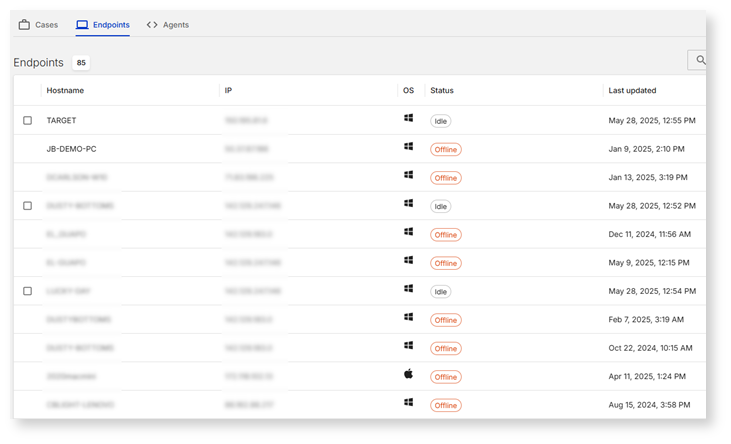
- Comprehensive collection: It captures relevant data like emails, cloud documents, local files, and browser history to identify evidence of misconduct.
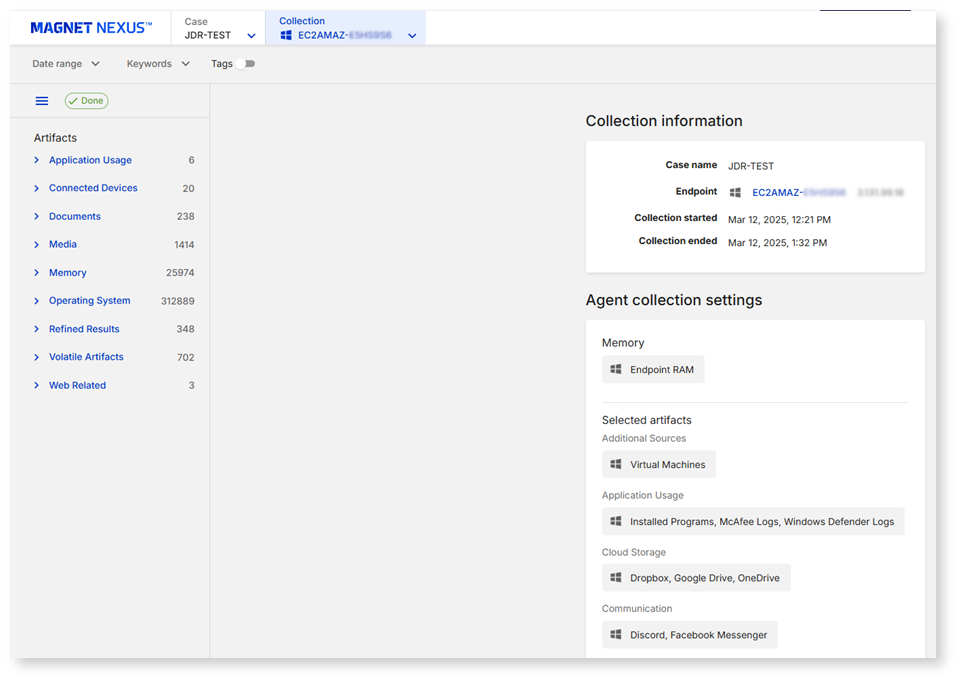
- Silent data acquisition: Data collection occurs unobtrusively to maintain forensic integrity and prevent tampering.
- Rapid analysis: Nexus’s analysis capabilities quickly determine if sensitive documents were accessed, downloaded, or shared externally prior to departure.
- Audit trail and defensibility: Ensures chain-of-custody tracking, metadata preservation, and thorough reporting, supporting potential litigation or regulatory reporting.
Use case 2: Deep forensic artifact analysis with Magnet Axiom Cyber
Scenario:
An employee is terminated due to performance issues, but management suspects the employee may have copied proprietary information prior to termination.
How Magnet Axiom Cyber supports this workflow:
- Focused artifact acquisition: Axiom Cyber acquires critical forensic artifacts from the employee’s laptop and external devices (e.g., USB history, recently accessed files, cloud synchronization logs).
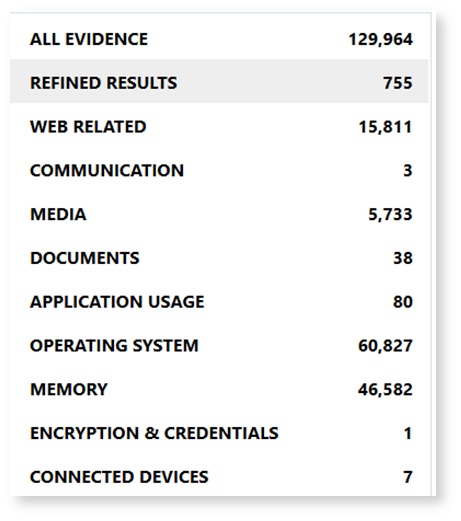
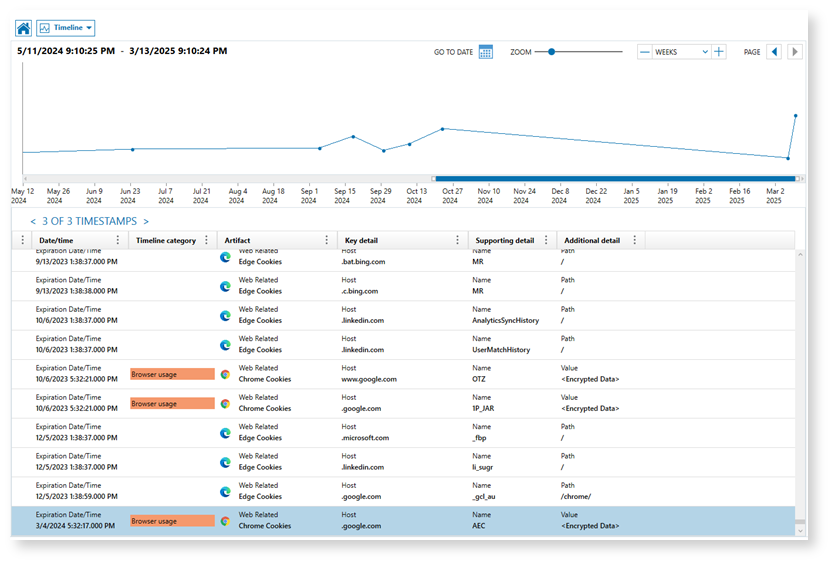
- Timeline reconstruction: Provides detailed timelines to reveal when sensitive documents were accessed, copied, or transferred externally.
- Cloud and application insights: Integrates with cloud storage and application-specific artifacts (e.g., Dropbox, OneDrive, Google Drive) to determine whether files were exfiltrated or uploaded to unauthorized accounts.
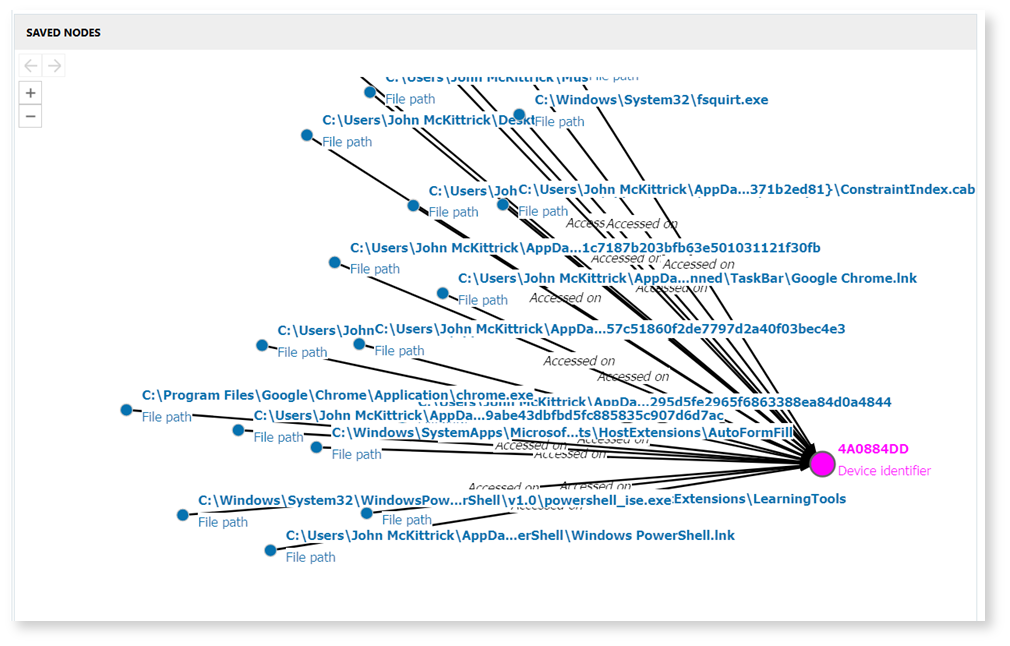
- Evidence visualization: Easy-to-use and easy-to-understand graphics illustrate exactly how and when the employee interacted with sensitive data, enhancing clarity for legal or compliance teams.
- Defensible documentation: Generates forensic reports with comprehensive details to support internal investigations or external legal proceedings.
Use Case 3: Targeted Mobile Communication Collection with Magnet Verakey
Scenario:
During an exit interview investigation, legal needs to preserve messages from a third-party mobile app used by an executive. These messages are stored in a location only accessible via a full file system extraction, making them invisible to a standard logical acquisition.
How Magnet Verakey supports this workflow:
- Uses category-based targeting to extract only the “communications” category, avoiding over-collection (at the full file system level to get all relevant data).
- Maintains forensic integrity with hashes, logs, and defensible acquisition records.
- Preserves only relevant data, protecting privacy while ensuring critical evidence is captured.
Conclusion
Employee departures, especially those involving access to sensitive information, require more than standard eDiscovery preservation. Digital forensics ensures comprehensive, defensible collections that include hidden, deleted, and system-level artifacts, while enabling targeted preservation to minimize risk and cost. When combined, tools like Magnet Nexus, Magnet Axiom Cyber, and Magnet Verakey give organizations the speed, scale, and forensic depth needed to respond effectively to the unique risks posed by employee departures—helping protect intellectual property, maintain compliance, and safeguard business integrity.
Want to see more eDiscovery content?